Project
Development
We start with the initial
vulnerability test and progress to each additional test as the project moved
forward.
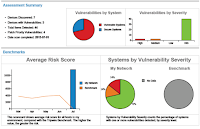
Original vulnerability assessment
25% high risks
After
installing Arch Linux before configuration setting applied 33% high / 16% medium
risk
After
installing dnsmasq and configuring 14% high / 14% low risk
After
installing and configuring snort 12% high risk
The goal of the project was to provide an affordable
security solution for a small to medium sized network. It was pretty much
determined from the beginning that the hardware platform would be a raspberry
pi. The undetermined was exactly what open source software solution would work
well with the Pi form the operating system platform to the layers of other
software that would be installed above and beyond the OS.
The other piece of the puzzle that needed
clarification had to do with the penetration testing process. There are many
tools available and endless opportunities to try and compromise a security
solution. New vulnerabilities are discovered each day. I found that the initial
penetration test was taking an inordinate amount of time to accomplish and so I
needed to define more clearly the scope of that part of the project. I adapted
the initial pen test to a more simplified vulnerability test due to time
constraints. I explained the difference between the two since in any
comprehensive security solution, especially as the network increases in size
and makes use of any external facing servers or services, you will want to include
pen testing at least once a year in your security solution.
I was glad that education was such an important part
of the goal of my project because in the end the information gathered and
provided has served to do just that. Provide an overall solid understanding of
the nature of the risks that are out there, and ways to mitigate those risks
and has exposed the danger of doing nothing at all and leaving the security of
your network to chance.
Also I want to reemphasize the dynamic nature of
network security, the need to wash rinse repeat, to not remain stagnate or
believe that it’s a problem that is once solved always solved. I mention again
the IoT (internet of things), and the idea that as things become more connected
there will always be concerns about making sure that the rogue elements that
exist will not be able to find and exploit security holes.



No comments:
Post a Comment